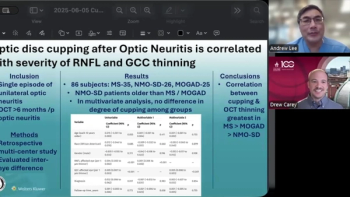
Why ophthalmologists are easy prey for cybercriminals
A perfect storm is brewing that may make ophthalmologists and office staff, with networked equipment, easy targets for cyber criminals. In a matter of days, cyber criminals can infect computers around the world. Sure, you can pay the ransom, but HIPAA fines and consultant fees, recovering from the damage to your reputation, loss of patients, and all the time and energy lost could bankrupt your practice.
Editor’s Note: Welcome to “
A perfect storm is brewing that may make ophthalmologists and office staff, with networked equipment, easy targets for cyber criminals.
Unfortunately, far too many health care professionals seem to be ready to battle with today’s cyber criminals.
Instead of giving up, let’s take a critical look at the threats and potential solutions.
How can cyber criminals make money off medical centers?
Beyond ransoming centers to unlock databases, cyber criminals can use patient information to steal identities; order new credit cards, open bank accounts, take out loans, and file false claims on your insurance. According to Reuters, selling patient records can be 10 to 20 times more valuable than credit card information.
Why?
The reason why is because credit card numbers can be changed overnight while addresses, employers, insurance numbers, and diagnoses can’t.
If that isn’t scary enough, cybercriminals could ransom patients on medical devices such as pacemakers.
Former Vice President Dick Cheney had the wireless feature turned off in his pacemaker.
Why are ophthalmologists easy prey?
Modern medicine has been pushed into a numbers game where optimal efficiency with low overhead is demanded. Few practices have dedicated IT staff that can protect, test, and monitor the security of the systems needed to keep an ophthalmology practice moving. Too often, this task is left to the staff member or doctor who has the most computer knowledge and spare time.
Combine this with the particular nature of ophthalmology practices and the vulnerabilities become frightening:
Courtesy of Sidd Chopra
- Private exam rooms where patients are left alone behind closed doors with access to equipment
- Waiting rooms with WiFi access
- Low tolerance for business disruption
- High premium on reputation
- Staff with little or no training in IT security or cyber hygiene
- Typically well-funded
Then, there is the imaging equipment. These, and similar devices, are driven by internal and external computers that are hard to update. Often, they contain patient information and are connected to networks.
A senior security engineer at Battelle estimates that 1 of every 4 medical devices is connected to a network. In of itself this is fine, but they are also situated in such a way as to give easy and discreet access to patients and others.
Diagnostic and life support equipment, as well as therapeutic equipment, such as surgical lasers, can be hijacked, corrupted, and even have their settings altered and safety measures disabled.
Courtesy of Sidd ChopraIt is predicted that by 2020, more than 25% of identified enterprise attacks will involve these and other connected devices that are part of the exploding Internet of Things (IoT). The consensus among security experts is that half of IoT products are insecure.
Some vendors are working to find ways to shield these devices from attack so that practices can continue to use legacy equipment securely.
If these devices are not properly backed up and restored, an attack can render some very expensive equipment useless.
How much is an attack going to cost you?
For large corporations, ID Experts estimates that the average cost to recover from a data breach is estimated as high as $2.2 million and Ponemon Institute reports that the cost is more likely $4 to $7 million.
Courtesy of Sidd ChopraErie County Medical Center spent nearly $10 million recovering from a massive cyber-attack this month- and that was just for this incident. They expect to pay an additional $250,000 to $400,000 a month upgrading technology, hardening systems and training employees.
Attacks on individual practices could easily run into the hundreds of thousands in expenses and productivity losses. Even if everything is restored, some practices may never recover from the bad publicity and the loss of patient trust.
If practices are not careful, cybercrime could be an existential threat.
Is it really this bad?
Cybercrimes are projected to cost the global economy over $6 trillion by 2021. The healthcare industry topped the list of most cyber-attacked industries in 2015, followed by manufacturing, financial services, and government and transportation agencies.
In 2016, “cybercrime cost the global economy over $450 billion, over $2 billion personal records were stolen and in the United States alone over 100 million Americans had their medical records stolen,” Steve Langan, chief executive at Hiscox Insurance, told CNBC.
Even the Department of Homeland Security and the White House are not immune as the recent
“The country is under siege right now,” said Jay L. Rosen, MD, chief executive of Tampa Bay Surgery Center.
What should you do?
Take cyber security seriously. Get an expert to review and secure your systems. Teach cyber hygiene to doctors, administrators, and staff.
Paul Lucas, chief financial officer of Georgia Retina in Atlanta, sends out an alert email to 13 doctors and over 140 staff members whenever a serious threat appears. Periodic reminders are vital to keep busy staff from forgetting.
Georgia Technical Institute’s cyber-physical systems security expert, Raheem Beyah, PhD, explains, “If we don't educate individuals and we don't do it consistently and regularly in a sort of mandatory fashion, then it doesn't matter about the software-it doesn't matter about the firewalls. None of the stuff matters because folks will click ‘yes’ or click ‘accept’ and then the malware is there.”
However, be careful trying to do this all on your own. John Copeland, PhD, network expert and founder of Lancope, explains that the tools needed “are designed for network experts to use and [not] medical people.”
It is a lot of work for a full-time physician to worry about. Dr. Copeland, whose company was purchased by Cisco Systems for $452 million, continues, “They really need to use the standard security practices, have some sort of firewall, have the hard disc encrypted, and have passwords that are hard to guess. The most important thing is to keep the operating system updated and keep the applications updated because there are continually vulnerabilities being discovered in the operating systems in a number of areas.”
For a list of do’s and don’t’s, visit
What’s the bottom line?
For years, cyber security experts have been saying that there are two types of companies: those that have been hacked, and those who don't know they have been hacked.
It may not have held true for medical practices but that seems to be changing quickly and if medical practices aren’t prepared, the result could be disastrous. Dr. Beyah advises, “It will happen at some point; we won't have a choice. We will see something much worse than what we saw in November.”
While some practices are still resisting practice medicine in the computer age, we now have to also pay to price for practicing medicine in the Internet Age.
In the coming months, at the
The good news is that medicine has long since known the best answer: an ounce of prevention is a pound of cure.
Sidd Chopra is systems developer with over 30 years of experience building critical systems and performing IT security audits for state, federal, military and corporate entities. He is the founder of
Newsletter
Don’t miss out—get Ophthalmology Times updates on the latest clinical advancements and expert interviews, straight to your inbox.